What Are Social Engineering Threats?
Social engineering threats are manipulative techniques used by cybercriminals to deceive individuals into giving away confidential information. Unlike traditional hacking, these attacks target people rather than systems. Think of it as a confidence trick but on a digital scale.
How Do Social Engineers Operate?
Social engineers use psychological manipulation. They may impersonate a trusted authority, create a sense of urgency, or offer something enticing. The goal is simple: get you to let your guard down.
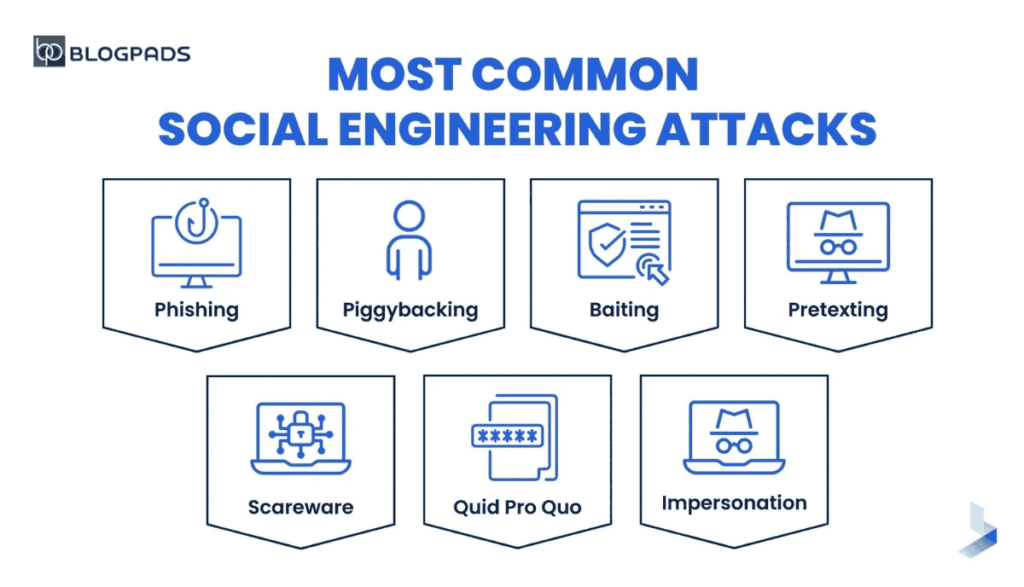
Types of Social Engineering Attacks
1. Phishing: The Most Common Threat
Phishing is like a wolf in sheep’s clothing. It often appears as a legitimate email or message from a bank or service provider, asking you to click on a link or share personal information. The link, however, leads to a fake website designed to steal your data.
2. Pretexting: The Art of Pretending
In pretexting, attackers create a fabricated scenario to trick victims into revealing sensitive information. For example, they might pose as IT support asking for your login credentials to “fix an issue.”
3. Baiting: Too Good to Be True
Ever seen a USB drive lying around and thought about plugging it in? That’s baiting. The attacker relies on curiosity to spread malware or steal data. Similarly, online baiting may involve offering free downloads that are infected.
4. Tailgating and Piggybacking
In physical spaces, these methods involve following an authorized person into a restricted area. For example, someone might pretend they forgot their access card to gain entry.
Why Are These Attacks Effective?
Social engineering thrives on human weaknesses. Trust, curiosity, and urgency are universal emotions. Combine that with a lack of cybersecurity awareness, and attackers have a recipe for success.
Real-Life Examples of Social Engineering Attacks
- The Google Docs Phishing Scam: A fake email asked users to open a document, leading to compromised Gmail accounts.
- The Twitter Bitcoin Scam: Hackers gained access to high-profile accounts, posting fake giveaways to steal cryptocurrency.
- CEO Fraud: Cybercriminals impersonated executives to authorize fraudulent wire transfers.
Warning Signs of a Social Engineering Attack
- Unusual Requests: Asking for sensitive details out of the blue.
- Urgency: Phrases like “Act now or lose access.”
- Suspicious Links or Attachments: Always think twice before clicking.
How to Protect Yourself and Your Data
1. Educate Yourself
Learn about common scams and share your knowledge. The more people know, the harder it is for criminals to succeed.
2. Verify Requests
Always double-check any unexpected request. If your bank emails you, call them directly to confirm.
3. Use Strong Passwords
A unique password for every account reduces the risk of a data breach.
Best Practices for Businesses
- Conduct regular employee training.
- Use multi-factor authentication (MFA).
- Monitor for unusual network activity.
The Role of Technology in Prevention
AI-powered tools can detect phishing attempts, while firewalls and antivirus software add an extra layer of security. However, no tool is foolproof against human error.
What To Do If You Fall Victim
- Report the incident to the relevant authorities immediately.
- Change your passwords.
- Monitor your accounts for suspicious activity.
Conclusion and Final Thoughts
Social engineering threats rely on deception, not technical skills. They remind us that sometimes, the weakest link in cybersecurity is the human element. By staying informed and cautious, you can outsmart the scammers and protect your valuable data.
FAQs
1. What is a social engineering attack?
It’s a tactic where attackers manipulate individuals into giving away sensitive information through deception.
2. How can I recognize a phishing email?
Look for generic greetings, suspicious links, and urgent language. When in doubt, don’t click.
3. Why are social engineering attacks so successful?
They exploit human emotions like trust, fear, and curiosity rather than targeting technical vulnerabilities.
4. Can businesses be targeted too?
Absolutely. Businesses face risks like CEO fraud and insider threats, making employee training crucial.
5. What should I do if I suspect an attack?
Don’t respond. Verify the request through official channels, and report suspicious activities to authorities or IT support.